SSL Decryption of Web Traffic at the Network Gateway
One thing I’ve realised from working with Palo Alto Networks firewalls is how much network traffic runs over HTTPS/SSL these days.
Having your web traffic secured with SSL encryption is great for when you’re using your banking website, but it also means that malicious traffic can be masked from your network’s security devices and pass straight through.
Quite the double edged sword.
Palo Alto Networks firewalls include App-ID technology, which allows you to identify network traffic no matter which protocol or port it is operating on. With App-ID you have an extremely detailed view of what is going on with your network traffic.
Here are some great examples of how SSL decryption of web traffic at the network gateway can help.
Preventing Proxy and Web Filter Avoidance
I started my IT career in the education sector, working in both primary and secondary schools.
One thing I learned early in my time in schools is that students are not happy when they are blocked from accessing something online. And when they find a way around the block word spreads fast, and every other student will know how to get around it within a few hours.
This is especially true when it comes to web filtering in schools. After all it’s hard for some students to go without checking your Facebook every five minutes, or accessing that latest viral video.
Internet usage in schools used to be limited to the computer labs, but today with laptop, tablet and BYOD one to one programs every student is carrying a device of some kind, and trying to get around the web filter is even more of a priority.
I have even seen student’s host their own proxy avoidance websites so they don’t need to rely on the well-known sites that are already blocked by category-based web filters.
Fighting these issues was a daily battle and is getting even more difficult these days with so much web traffic being encrypted over HTTPS connections and virtually invisible to network security devices.
Enabling SSL decryption of web traffic at the network gateway allows you to see exactly which applications are the source of traffic that is going over HTTPS.
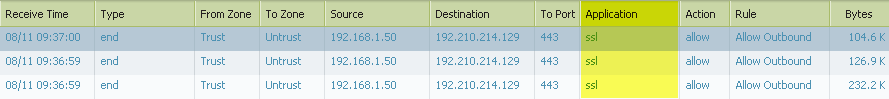
Here is what the firewall logs look like when going to a popular HTTPS proxy avoidance website.
All we can see is that the application is SSL, we are unable to see what application is inside that SSL encrypted tunnel.
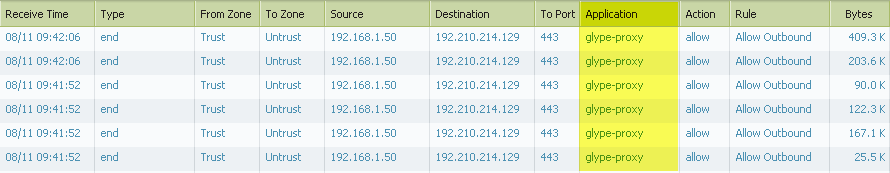
Let’s have a look at the firewall logs after we turn decryption on.
The Palo Alto Networks firewall is now able to look inside the SSL tunnel and using APP-ID identify the Glype-Proxy application.
Glype Proxy is a free web-based proxy script written in PHP. It allows people to quickly and easily set up their own proxy site and very popular for getting around network filters. Just searching for “Powered by Glype” returns 81,700 results. That’s a lot of websites that need to be blocked.
With decryption and one security policy using App-ID on the Palo Alto Networks Firewall you have successfully blocked all access to these sites, no matter how many more are created every day.
Detecting Malicious Network Traffic Hidden by SSL Encryption
Do you have virus scanning enabled on your gateway? Even if you do, without SSL decryption you aren’t protected from malicious payloads coming over the network in SSL encrypted connections.
All you can rely on is the antivirus software being up to date on your workstations and servers.
SSL decryption at the network gateway is the only way that threat prevention engines can scan the malicious data that is hiding inside that SSL encrypted traffic, so that you can protect your network at the edge instead of relying only on your internal antivirus protection.
Let’s take a look at an example using the good old EICAR virus test file to demonstrate what happens.
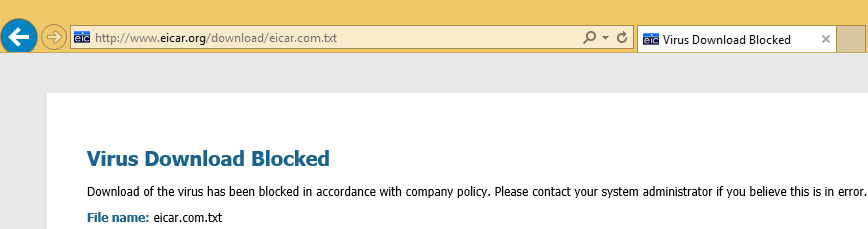
First, SSL decryption on the network gateway is disabled, and from a workstation the HTTP URL of the EICAR test file is accessed. The Palo Alto Networks firewall threat prevention engine detects the EICAR file in the unencrypted HTTP connection and blocks the download.
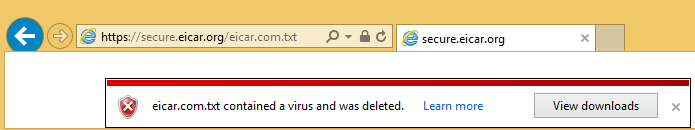
Now let’s try the HTTPS URL of the EICAR virus test file.
Oh no, the file downloaded to the workstation without being blocked, but luckily I have my antivirus software up to date and it detected and removed the EICAR virus file.
Now this is only a file built for testing anti-virus engines, but you can imagine the consequences if it was something nastier and the workstation’s antivirus software wasn’t up to date?
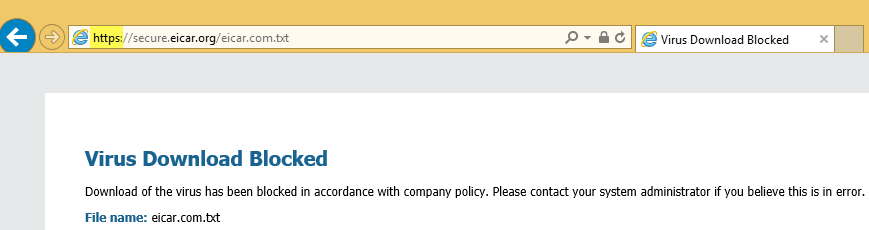
Now we’ll turn on the SSL decryption policy on the Palo Alto Networks firewall so the threat prevention engine can inspect the encrypted traffic. Let’s go to the HTTPS URL of the EICAR virus test file again and see what happens.
Denied, perfect! Thanks to SSL decryption and App-ID the virus is detected and blocked at the network gateway, instead of allowing it into the network.
Preventing Data Loss and Unauthorized File Sharing
There are a lot of cloud-based file sharing applications around (Dropbox, OneDrive, MediaFire, Mega, etc.) today.
All of these file sharing applications allow the uploading of files over HTTPS. Once this encrypted SSL tunnel is established your security gateway that isn’t doing SSL decryption won’t be able to log, scan or block the files being uploaded.
This doesn’t apply only to end users uploading data either, it could easily be a piece of malware stealing your data and uploading it to the internet over HTTPS.
Enabling SSL decryption on a Palo Alto Networks firewall gives you visibility of the files passing through the network gateway, and also allows you to implement data loss prevention to stop sensitive data from leaving your network.
Concerns about SSL Decryption at the Network Gateway
Decrypting SSL traffic at the gateway is a sensitive issue for some businesses, mainly due to concerns around privacy of employee’s personal information such as banking data or online shopping activities.
The Palo Alto Networks firewall allows you to have fine grain control over what you do and do not decrypt. You can exclude or include particular networks, specific users or website categories.
For example, you can choose to inspect all web traffic except for Financial Services, Government and Online Shopping. This allows you to assure your end users that you are only decrypting what is necessary in order to protect them, and your entire business, from the threats that exist on the internet.
Want to Know More?
Contact Idea 11 to schedule a demonstration or arrange a test drive of a Palo Alto Networks firewall in your business.